I’ve come back to update my article form 2021 to add the revaltions that alternative data streams were used in the famous Stuxnet virus. Read to the bottom for the Stuxnet connection information.
Notebook LLM Audio Podcast Version
Hacker Basics: How to Hide an Executable File Inside and Text File
I was pretty impressed the first time I watched someone demonstrate this. I was like, NO WAY! I really thought that this was some wizard level hacker stuff.
I’m no wizard level hacker, although I aspire to be, but I should be good enough to show you how to embed a simple calculator app inside a text file using an alternate data stream.
A big thank you to Cyber Security Expert, Malcolm Shore who presented a similar example in his Cyber Security Foundation online course I recently completed.
How Do Alternate Data Streams Work?
Way back in the old Wild West days when we had the DOS operating system, files used to be simple strings of data. Files are read btye by byte.
Later, in the NTFS file system, files are complex structures. NTFS files at a minimum contain a section called $Data where data is read by an application. $Data is the Data Stream.
Files may have many other sections or streams other than just the $Data section. This is what we call “Alternate Streams”.
THIS IS IMPORTANT: Windows only recognizes data in the $Data section so any data we put in an alternate data stream is not read by the Windows Operating System. We cloak data we want to hide in an alternate data stream. That’s the basics of how this works.
The data we are hiding could be a malicious malware payload or encrypted espionage message for our spy ring but in this example, it is just the simple calc.exe file you can find on any Windows PC for the last 20+ years.
Creating an Alternate Data Stream in a Text File
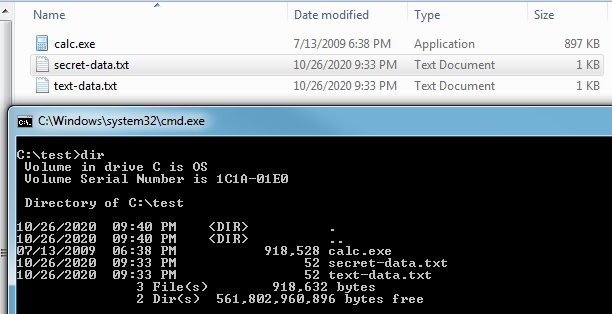
The screenshot below shows the three (3) files we’ll be using in this demonstration.
- Simple text file with some string data.
- calc.exe application or executable binary file
- Secret text file with some string data
We can see the size of the text file is just 1 KB and the calc.exe file is 897 KB.
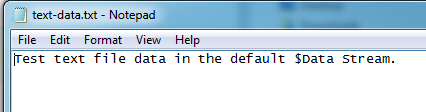
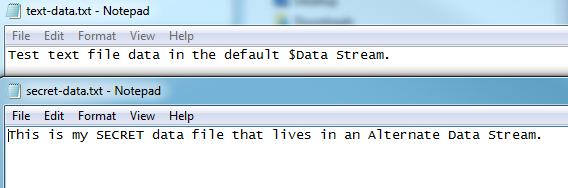
If we open the text-data.txt file with Notepad we’ll see just a simple line of text and the same with the secret-data.txt file.
To hide our secret message inside the the text data file, we’ll use this command line command.
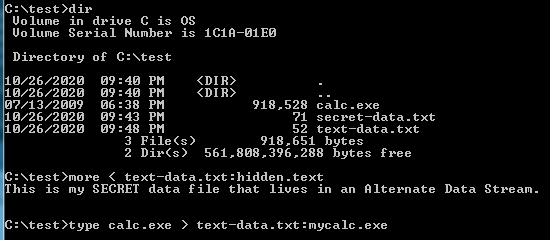
C:\text\>type secret-data.txt > text-data.text:hidden.text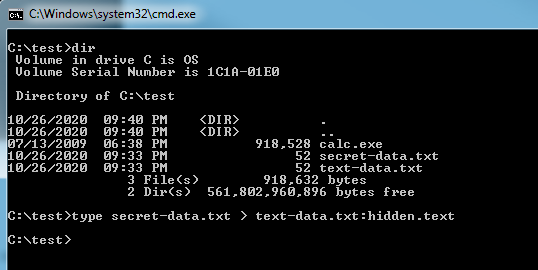
Screenshot of Alternate Data Stream: Insert Hidden Text
Below is a screenshot of the command line command “type” that we used in this example to insert our secret-data.txt file into an Alternate Data Stream inside of another text file.
If we type the command “more” we can look for the secret message.
The screenshot below shows the text file that contains our hidden text being opened in Notepad where we can’t see the hidden text we saved to the file. If we type the command line command below, we can read the hidden text we wrote to our Alternate Data Stream by keying in on the specific data stream.
c:\test>more < text-data.txt:hidden:text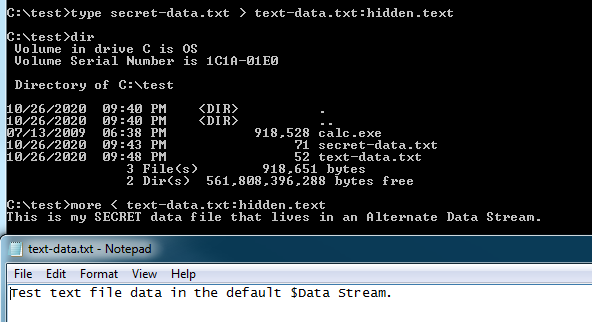
Hiding an Executable Inside a Text File
Hiding an executable file inside a text file using the exact same Alternate Data Stream technique we just used in the the Secret text file example above but this time we’ll simply replace the Secret text file with the Windows Calculator application executable file.
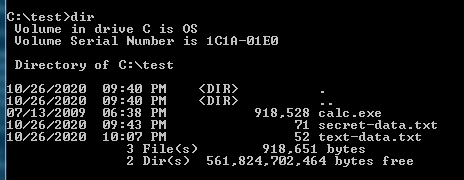
The screenshot below shows the command line command to save the calc.exe file in an Alternate Data Stream in side our target text file.
Notice this time, the Alternate Data Stream is named “mycalc.exe”. Don’t get to hung up on this, it is just a name that is basically meta data that is saved with the data that we can use to filter the data we get out of the file. I hope that makes sense.

Important to note at this point that the file sizes didn’t change when we inserted the calc.exe file. It is still showing 52KB.
How to Execute a File Saved in an Alternate Data Stream
To execute a file you’ve stored in an Alternate Data Stream, we’ll need to use the wmic command as is done in the following example.
c:\test>wmic process call "c:\test\text-data.txt:mycalc.exe"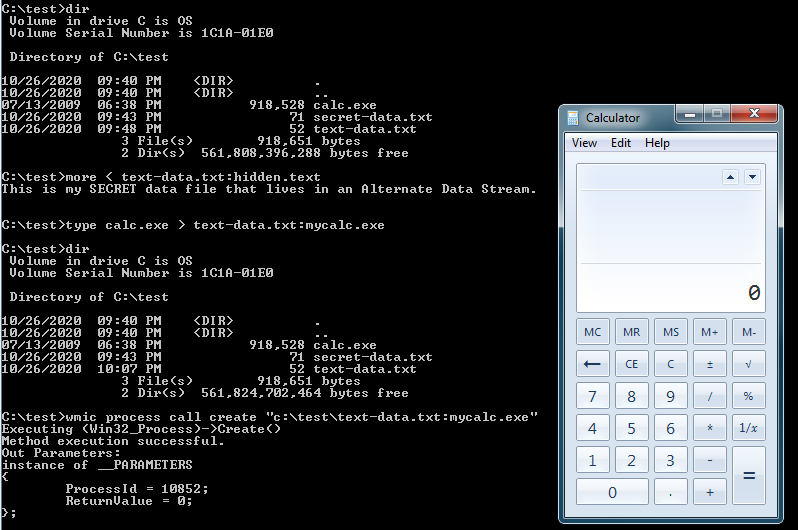
As you can see from the working example above, I was able to embed the calc.exe file inside as well as text file and a secret message.
If the data is text we just need to indicate which stream we saved the data in to retrieve it.
If the data we hid was an executable file, we’ll need to use the Windows “wmic” command line command to call the executable from inside the text file by keying in on the Alternate Data Stream name.
Alternative Data Streams and How it was used in the Stuxnet Virus
In summary, the technique is crazy easy to pull off without any 3rd party hacking tools. It just requires a little Windows Operating System inside knowledge but is something every good hacker should know.
For background, Stuxnet, a highly sophisticated piece of malware discovered in 2010, targeted SCADA systems and is best known for reportedly disrupting Iran’s nuclear enrichment infrastructure. One of the notable techniques used by Stuxnet for hiding and executing its components was leveraging Alternate Data Streams (ADS) on Windows operating systems.
In the case of Stuxnet, it used Alternate Data Streams in several ways:
Alternate Data Streams allow data to be attached to files without affecting the file’s functionality or visibility in most file browsers. Essentially, ADS is a feature of the NTFS file system that allows the storage of data in hidden streams alongside the main file content. This feature can be used for storing metadata but can also be misused for more malicious purposes.
- Hiding Malicious Code: Stuxnet hid its own code within ADS of legitimate files. This method of hiding helped it evade detection by many antivirus programs at the time, which typically scanned only the main data streams of files.
- Executing Code: Stuxnet was able to execute the code hidden in these streams seamlessly. Since the operating system itself supports the execution of files from ADS, this allowed Stuxnet to run its payloads without drawing attention to itself by creating additional visible files on the system.
- Persistence and Stealth: By using ADS, Stuxnet ensured that its components remained on the infected system and could be executed without direct user interaction, thereby maintaining persistence on the system while remaining stealthy.
The usage of ADS by Stuxnet is a prime example of how cyber threats can exploit lesser-known features of an operating system to conduct sophisticated and covert attacks. This technique complicates the detection and analysis of malware, demonstrating the need for advanced security measures and tools capable of inspecting such hidden streams in the file system.
Who Created the Stuxnet Virus?
The origins of the Stuxnet virus have been subject to extensive analysis and speculation within cybersecurity circles and international media. Although there has never been an official confirmation from any government, it is widely believed that Stuxnet was developed and deployed by the United States and Israel as part of a covert operation aimed at disrupting Iran’s nuclear enrichment capabilities.
Stuxnet’s sophistication and the specific nature of its target—centrifuges used in nuclear enrichment at Iran’s Natanz facility—suggest that its development required significant resources and expertise, further pointing towards state actors rather than independent hackers or smaller organizations.
Several investigative reports, notably by journalists at The New York Times and researchers in cybersecurity firms, have linked the development of Stuxnet to a collaborative effort between the U.S. National Security Agency (NSA), the Central Intelligence Agency (CIA), and the Israeli military. The operation, reportedly code-named “Olympic Games,” was said to have started under the George W. Bush administration and continued under President Barack Obama.
I hope this helped somebody!
~Cyber Abyss
